Learning management systems operate large amounts of sensitive data, from student grades to personal information to the organization's intellectual property. All that makes LMS a tidbit for hackers, and statistics second that: in 2022, the education and research sectors were the most targeted globally.
According to Statista, organizations in education faced 2314 weekly cyber attacks on average. It's a 44% increase from 1605 weekly attacks in 2021. Cybercrimes are at an all-time high, and each LMS faces a growing risk of data breaches, malware attacks, and misuse of personal information.
Here's another not-so-fun statistic by IBM: the global average cost of a data breach in 2022 was $4.35M. Compromised companies bear a lot of long-lasting consequences:
-
reputational damages and lost clients, thus lost profits
-
hefty fines
-
spending on informing everyone affected by the breach
-
spending on a task force putting out the fire
-
spending on recovering IT assets and infrastructure
-
changing vendors and infrastructure.
Add to it that LMSs are usually integrated into organizations' broader data management systems and that LMS vulnerabilities thus can open a doorway into the company's entire system, and you'll see how crucial data protection is for a learning platform. So let's talk about what makes some solutions more secure than others.
What security threats LMSs face
Learning management systems can be compromised like any other software product, usually resulting in a data breach. Here's what can lead to it:
Accidental exposure
It happens when someone leaks data by mistake. For example, an employee can mess up the authorization setting and open access to a database, lose a device with data or user credentials, or straight up send data to the wrong place or person.
Insider job
Some team members can do the same acts maliciously, e.g., out of spite or for a reward.
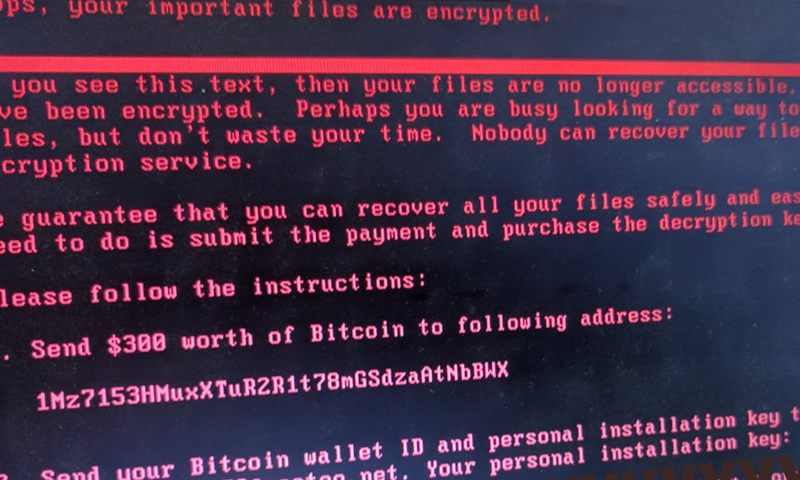
Interception of the data in motion
When the data is transferred from one point to another — sent to the cloud or exchanged between different networks or applications — there is a risk it will be intercepted in the process and used to get into the company's systems.
Unauthorized access
Finally, the systems can be hacked. Suppose the intruder finds a vulnerability and stays uncaught. In that case, they can do pretty much anything — steal data, install spyware, spread the malware further down the company's network, block access to the systems to get a ransom, or obliterate them.
Cybersecurity's motto is that you should treat an attack as inevitable and actively try to postpone it. That's why proper security measures focus on continuously delaying the breach and minimizing the damage when the breach has happened.
Security measures an LMS should implement
There are not so many government regulations and guidelines on cyber attack prevention, so it's on the conscience of the LMS developers and owners how safe their platform is. Diligent cybersecurity boils down to thoughtful product design, regular audits, and constant defense improvement. However, there is a set of security measures an LMS must employ to be considered safe.
Data encryption
Encryption algorithms convert plain text into unreadable gibberish that can be deciphered only by someone with the key to convert it back. That means that even if your data gets intercepted while you send it somewhere over the internet, the thief won't be able to make any sense of it.
Regular password changes and multi-factor authentication
Stolen credentials are the easiest way to sneak into the system. That's why it's critical to use unique, strong passwords, change them at least once every three months, and use several forms of authentication: temporary codes, second devices, or biometric authentication. The more security layers there are, the harder it is for a hacker to brute-force their way into your systems.
Strict user roles and access levels
After verifying the user, the next step is to decide what data they can access, and stinginess goes a long way here. Access to sensitive data should be granted only to those who absolutely need it, especially in a remote workplace. One of the most popular and straightforward approaches is role-based access control which assigns permissions to users based on what's necessary for their job function.
Other approaches are discretionary access control, where the data owner decides on access ad hoc; mandatory access control, in which a central authority assigns access rights based on information clearance; and attribute-based access control, where the access to data is dynamic and depends on a user's location, position, etc.
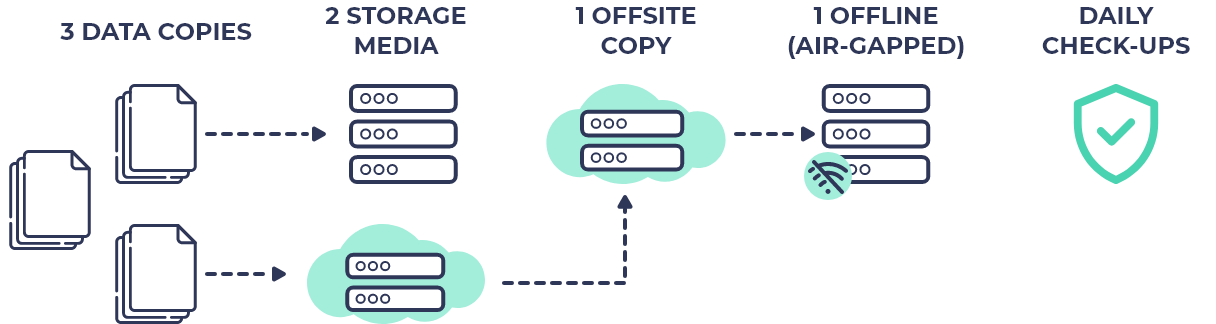
Data backup
Data backup doesn't prevent a company from an attack or other emergencies. However, it ensures that the data can be restored if things go south.
Content protection
Enforcing copyright on intellectual property helps protect learning content from unauthorized distribution and plagiarism. Again, it doesn't prevent data from being stolen per se, but it gives leverage in potential legal disputes.
Privacy regulations compliance
Legislations such as GDPR or CPRA address data misuse and introduce the "privacy by design" principle, which means that if the product collects and uses personal data, its design should account for that:
-
Users must know how and why the data is collected and what 3rd parties can access it.
-
Users can correct their data, limit its use, or opt out and erase it at any moment.
-
The product must gather the necessary data only and have appropriate technical and organization measures for handling and processing the data, such as encryption, regular check-ups, and trusted 3rd party partners.
Compliance with data privacy laws facilitates LMS security.
Security protocols update
New security vulnerabilities are discovered and patched daily, so keeping all the software up-to-date is essential to ensure you don't leave these doors open for ill-willed actors.
Regular comprehensive audits
It's highly recommended to measure up the system's security against industry standards and federal regulations every once in a while. An independent audit will point out exact shortcomings across the previously mentioned aspects, like access control or password policies, and provide recommendations for improvement.
And it might be even more informative to perform penetration testing where a certified specialist identifies vulnerabilities by trying to break into your systems so that you can close them up before a malicious attack exploits them.
Response plan
Unfortunately, no preventive measures give a 100% guarantee against a successful attack, so each organization should have a detailed plan for dealing with a data breach.
Many countries have regulations, like GDPR, that cover how the company must respond upon discovering an attack. These actions include finding and containing the compromised systems, notifying the relevant supervisory authority and people whose data was stolen, and patching the vulnerability. The key is to act quickly, as the damage increases each day.
Ideally, all the measures mentioned above should be implemented by default.
Security by design — the forethought that counts
Overall, instead of slapping some password policy on top of the existing product, the LMS developers should assess security risks and think through how to build the platform to mitigate them from the get-go. This holistic approach is called "security by design."
There are several security-by-design frameworks that you can use as guidance. To name a few:
NIST SP 800-160v1r1
The US National Institute of Standards and Technology develops principles of engineering trustworthy and secure systems that can be used as a basis for educating and training security engineers.
Microsoft Security Development Lifecycle (SDL)
Microsoft developed a software development policy in the early 2000s that allowed the company to tackle security compliance while reducing development costs. The guidance is publicly available and includes best practices, tools, and processes Microsoft uses internally, including scenarios using the cloud, Internet of Things, and artificial intelligence.
AWS Security by Design framework
Amazon cloud services have formalized and automated every little nook and cranny regarding security controls and audits by designing templates for access controls, encryption, logging, etc. And everyone can use their approach for scalable security and compliance.
OWASP Software Assurance Maturity Model (SAMM)
The SAMM project is an open framework for formulating and implementing a tailored software security assurance program focusing on measurability.
Each of these frameworks follows the same principles. The first is minimizing the attack surface — entry points susceptible to attacks. It makes intruding harder and keeping defenses up easier.
Second, every security layer can be breached; that's why you should stack as many of them as possible so that even if one measure fails, the system remains uncompromised. This is called a defense in depth principle. Multi-factor authentication falls in this category, for example.
The third and fourth are secure defaults — a certain security baseline all users, regardless of their roles, must comply with, and the least privilege principle of giving users the bare minimum access to decentralized data, just enough to do their job. In this case, a user's misdeeds will impact only a tiny restricted section of the system.
Finally, the open design principle says product safety shouldn't rely on secrecy. Instead, it should be able to remain secure even if its source code and security configuration gets disclosed. Moreover, putting the source code out there in public can benefit the platform's security even more.
Security benefits of open-source LMS
In 2021, Red Hat's global survey showed that most companies consider open-source software more secure than proprietary, which is a reasonable assumption. The logistics of the open-source community facilitate security in many ways:
-
Open libraries contain many ready-to-use assets. Using these assets allows developers to spend less time and money creating features from scratch and focus more on other tasks, including security engineering.
-
And the open code submitted by big sharks like Google opens smaller teams access to innovation that translates into all-around better products.
-
As the code is transparent and anyone can contribute to it, open-source LMSs are scrutinized by bug bounty hunters and the interested public, which is basically a free external audit. Plus, there's always someone out there who knows how to improve the solution.
-
Another consequence of being scrutinized is the prevalence of security by design approach to software development, as developers don't want their code to become a dusty patchwork blanket no one uses.
-
Open-source LMSs can be modified if an organization has specific security needs — custom user roles, data management configuration, or 3rd party tools integrations. Given that the LMS's source code is free, the company can allocate resources to some extra security measures.
Choosing a secure LMS: what to look for?
Data security and privacy are critical concerns for learning management systems and their users. As the education sphere becomes increasingly digitized and cyber attacks on LMSs are becoming more frequent, LMS owners are responsible for implementing comprehensive security measures, from strict password policy to regular audits at the very least.
More preferably, LMS should be developed using security-by-design principles to ensure security is built into every stage of the software development lifecycle. One of the ways to find such a platform is to look into open-source software that provides additional security benefits such as transparency, cost-efficiency, flexibility, and community support.
Opigno LMS is an open-source platform compliant with the highest corporate security standards, including data encryption, private file system, multi-factor authentication, and flexible access control configuration. If you'd like to learn more about how we ensure our solution is secure, please get in touch with us by following this link.
And if you'd like to check if your learning platform is up to standards, we also offer an LMS security audit service.
Published on May 2, 2023.